Hi Gents,
How i prevent to user to install any software.
Hi Gents,
How i prevent to user to install any software.
You can create containment block rule for all exe files which will help you with stopping the execution of such files.
You can also block using AD GPO
with the help of below scripts you can get notified of any installation of software
https://scripts.xcitium.com/frontend/web/topic/notify-on-software-installationmsi
https://scripts.xcitium.com/frontend/web/topic/script-to-alert-if-any-new-software-installed
Thanks @ nivedithab. Now i can prevent to user to execute .exe but after this user system performance is very very slow and some time cant access internet also.
When an issue arises in which logs are needed for investigation, there are two options:
Run the logs via a Procedure on the problematic endpoint via the Portal.
Run the log collection applications locally on the problematic endpoint. (This is just in case if the procedure via the Portal happens to fail).
If you plan on running the procedure via the portal it can be done by the following steps:
Devices > Device List > Click on the Device:
Next click on Run Procedure:
Be sure to run the Procedure as “LocalSystem User”:
Type in C1 and run the first procedure as highlighted in the below screenshot:
This will then start the process to collect the cisreporttool logs from the endpoint.
Cisreporttool logs are needed for investigating issues related to any active component within XCS: AV, FW, HIPS, Containment, etc.
If you run the procedure via the portal and it is successful, please include the device name in the support ticket so we can quickly search our SFTP for the logs and begin to investigate.
Here is the download link for the cisreporttool in case the procedure happens to fail:
http://download.comodo.com/cis/download/installs/cisreporttool/cisreporttool.exe
If you run the cisreporttool locally on the endpoint, an output file will be stored in the location where you run the tool from.
Please share the cisreporttool logs in the support ticket so we can further investigate, typically you can quickly share it via OneDrive. Just be sure to remove any permissions on the shared link.
Now, in the case of Performance/Slowness issues, and you suspect it to be caused by XCS, Performance Logs are needed for us to investigate and find root cause.
We also need a set of fresh cisreporttool logs after the Performance Logs have been collected.
It is important to remember, Performance Logs must be collected at the time the issue is occurring.
You don’t have to run the Performance Log tool for more than 10 minutes.
After the Performance Logs are collected, then collect the cisreporttool logs.
I have attached the procedure to collect Performance logs to this email.
Please import it into your console >>Ready to Review>> Approve it >> Run on Endpoint when necessary.
When the user is having Performance/Slowness issues, send this procedure to the endpoints and it will do the following:
It will download and install the windows ADK (Assessment and Deployment Toolkit).
sets the DisablePagingExecutive value to 1 in the registry.
puts the SlowIo2.bat in Windows Performance Toolkit folder.
Creates task scheduler to run a given script to collect and upload performance log.
Restarts the system.
Task scheduler runs the given script to collect and upload performance log to SFTP server to the given location in the script.
Again, if you run the Performance Logs script, please include the device name in the support ticket so we can quickly search for it in our SFTP.
Now, in the case if either procedure happens to fail, that is when we would need to collect the same information via downloading the tool.
You can download the Performance Tools here from my OneDrive and run it on the problematic endpoint. The zip file has an instructions.txt file:
Also, here’s a quick video on how to collect Performance Logs via the same tool:
Collecting Windows Performance Logs.mp4
Please share the Performance logs in the support ticket so we can further investigate, typically you can quickly share it via OneDrive. Just be sure to remove any permissions on the shared link.
Again, the applications are needed only if either procedure fails, just as backup.
In the case of any application is getting blocked:
Try to disable the XCS components and check again, right click the XCS tray icon and disable the Antivirus component and check if the application is opening as expected.
If it opening as expected with the AV component, move on other to components and disable it one by one (Containment, HIPS, Firewall) this way we can find out which component of XCS is blocking the application, based on the result we can add the exclusion rules to exclude the application.
Enable / Disable AV, Firewall, Auto-Containment and VirusScope Easily
How to define file groups as exclusions to Antivirus, Firewall, HIPS and Containment
https://wiki.xcitium.com/frontend/web/topic/how-to-define-file-groups-as-exclusions-to-antivirus-firewall-hips-and-containment
If after the above repeated steps and you are still facing the issue, please follow the steps to collect cisreporttool logs along with the device name.
Hi @ nivedithab,
the log has been forward thrgh as you mentioned.
After i enable containment i cant run any .exe application even that application already install.
i want to prevent the user to install new software.
I will check for the feasibility with backend team and get back to you
Is there any update?
I have checked with the backend team and and they have shared their feedback on the solution you are requesting , please find their comment given below.
XCS is about protection from Malwares, but not about blocking Trusted files. If you want to block some particular software installation, in this case he can create Containment rule using name of the installation package to block it. But it cannot auto detect the new software installation and automatically block it without any rule.
As of now XCS does not have such built-in functionality. You may find the possible solutions given below for your requirement
Blocking applications installation is not trivial task, because first of all XCS is security product, but not applications manager software.
From existing XCS abilities there can be several approaches , but they have disadvantages, of course, because of mentioned above:
Blocking by hash. The disadvantage is that it is almost impossible to track the hashes for all software versions in time, including new versions.
Blocking by filenames, path. The disadvantage of this approach is that it fails if the file has been renamed and does not match the specified mask.
Blocking by software Vendor. The disadvantage of this approach is that ALL the software signed by blocked vendor will be blocked AND this option can be configured locally only , but cannot be managed from EM portal.
Available options explanation:
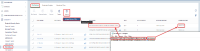
By setting the Malicious rating for such files, you will prevent this files from running. The disadvantage of this method is that it is necessary to list all hashes and add new hashes when new versions are released. The advantage is that it is enough to add hashes in one place and this approach will work even if the user renames the file.
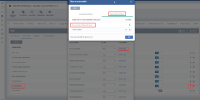
For convenience, you can use File Groups. For example “Remote Control Software” group:
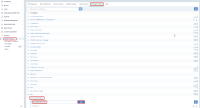
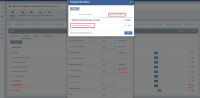
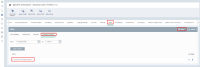
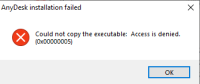
In this case, the following error will appear:
Pay attention , ALL the software signed by this vendor will be blocked.
You may submit feature request on https://feedback.xcitium.com